What is Arcium? How does it work? | Deep Dive
Learn how Arcium is the first confidential computing network utilizing Solana as a consensus layer.

Introduction
Back in 2023, a protocol aimed at providing ZK privacy on Solana went live on mainnet; that protocol was Elusiv. Elusiv went live with their private token swaps which was a huge success may I add, and so grew their vision keeping in-line with the goal they had planned - Enabling privacy and compliance to co-exist. This aim led to building a more advanced architecture that we now know as Arcium.
From @elusivprivacy to Arcium - a story of evolution, expanded vision, and an unwavering drive for bettering all of Web3.
— Arcium ☂️ (@ArciumHQ) May 15, 2024
Gather around as our umbrella just got quite a bit bigger.. 🌂☂️👇 pic.twitter.com/ire31yaonW
Arcium is a parallelized confidential computing network. I know, I know, big words. In simple terms, Arcium allows you to process and collaborate on data securely on-chain. It ensures that no intermediary can see the details of the data you're sending or receiving, keeping it confidential.
It does this with a lot of cool stuff like MXEs, MPC setups and zk-proofs, everything which we'll be diving into later in this blog!
Arcium recently completed their strategic funding round of $5.5 Million led by Greenfield Capital, Coinbase Ventures, Longhash Ventures and more bringing their amount raised to a total of $9 Million.
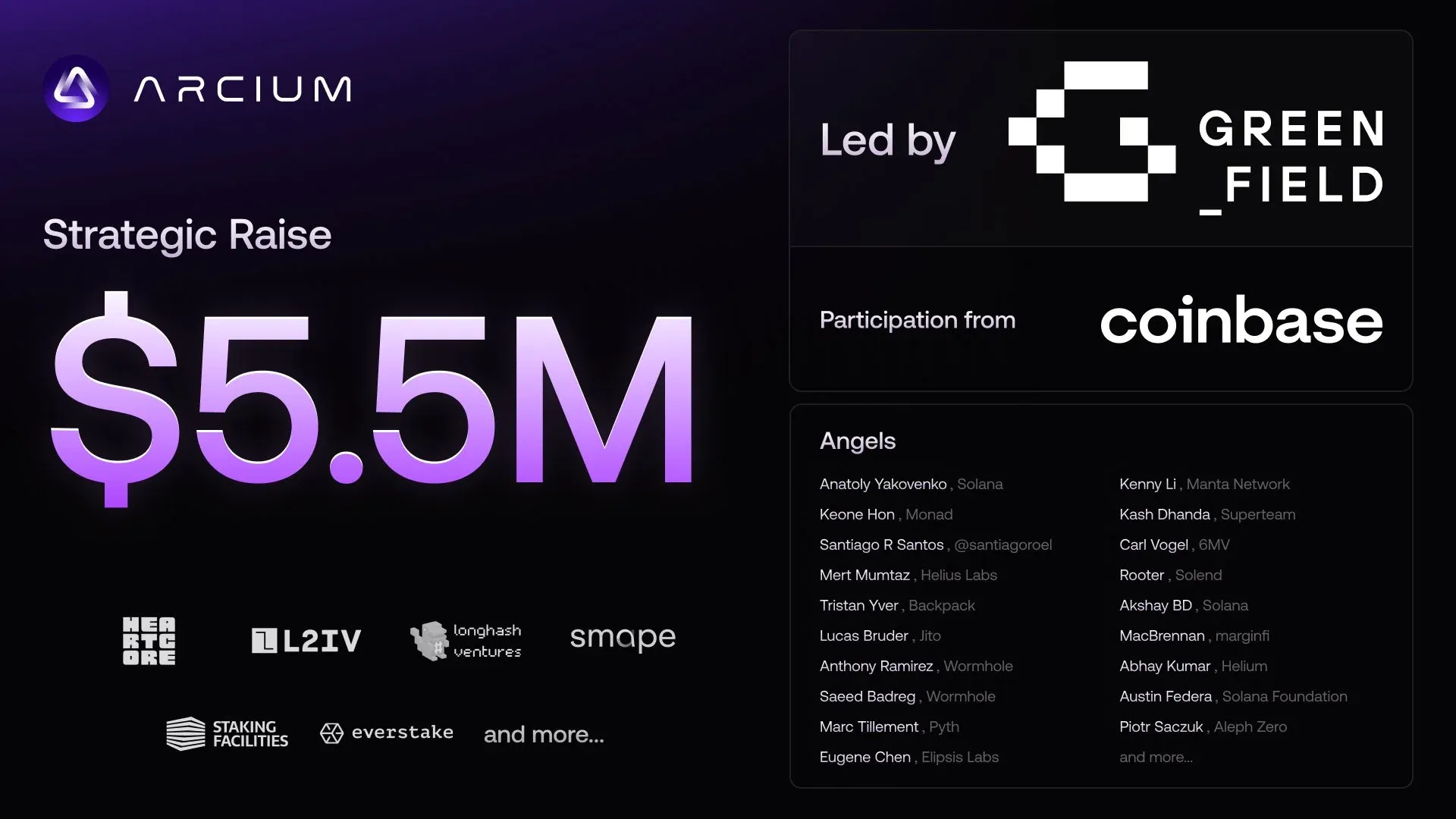
With that intro aside, sit back, relax, grab a cup of coffee because this is gonna be a long read.
We're about to unfold a new Arc-ium of private computing! 👀
Confidential Computing
As we mentioned earlier, Arcium is a parallelized confidential computing network. Thus, to understand Arcium, we have to first understand confidential computing. Well, it's pretty self explanatory. Confidential means secret and computing means any calculation being performed. Thus, confidential computing means any calculation being performed without decrypting or leaking any encrypted data i.e keeping the secrets.... well, secrets.

MPC Tasks
They achieve this by utilising a distributed architecture of nodes that are capable of Multi-Party Computation or MPC tasks. In simple language, each node processes a part of the data without revealing it to the others thus it requires multiple nodes or parties to compute a single task. This whole process also involves these nodes communicating to each other for computed results and then combine that to obtain the final output which is then relayed to the receiver.
Why is MPC so important to Arcium and what are the differences between it and FHE? 🤔
— Arcium ☂️ (@ArciumHQ) June 25, 2024
They form the groundwork for our Multi-Party execution Environments (MXEs), which define the MPC parameters on the Arcium Network.
A quick 🧵👇 pic.twitter.com/9z1Zhf1jYh
Using such nodes helps in reducing any single point of failure by distributing tasks while also ensuring that the data remains confidential at all times as they don't share the inputs but only the outputs.
Note that on Arcium Network, these MPC nodes are referred to as Arx node so whenever Midwit says Arx nodes, think MPC nodes
Arx Operators
These Arx nodes are run by what we know as Arx Operators on their physical hardware to perform the computations and earn rewards, something that we'll cover a bit later.
An easier equivalent of this would be how Miners (Arx operators) mine tokens on their systems (Arx nodes).
To start computing, these operators must need to:
- Specify the computational resources their node can provide to the network
- Stake amount of tokens that are proportional to the resources their node can provide
- and specify if they node is equipped with a Trusted Execution Environments or TEEs. Don't worry, we'll cover everything!
There are various types of MPC protocols which differ in the task that they do, the cryptographic technique used and a lot more which we aren't touching in this blog. You can check that out in Arcium Network's documentation
Arcium Architecture
Now that we understand the vital principle of the Arcium network—confidential computing— let's combine it with Arcium's architecture.
In this section, we'll examine each component individually and then combine them to reveal the complete picture of how it all works.
Let's jump right in!
Computation Customers
This is just a hi-fi way of saying the users of the Arcium network. They purchase confidential computing services on the network which is then used to reward Arx operators and Third party delegators for their resources.
The computation customers or users can also create a group of nodes which is called as Clusters to execute specific computations or tasks. The users can create these clusters based on certain requirements and properties like reputation and trustworthyness of the node, whether they have TEEs or not and other factors.
Trusted Execution Environments or TEEs
If you've read our thread on Switchboard, you would have probably seen this term being used. So, what are TEEs?
Well, TEEs are secure areas in a processor that offer more security than the usual operating environment. They keep the code and data inside them safe from other software processes, including the operating system. Switchboard was using Intel's SGX or Software Guard Extensions for TEEs, however, there are other TEEs as well including ARM's TrustZone and AMD's Secure Encryped Virtualization or SEV.

These TEEs while offer security and confidentiality to the code and data inside them, there are some cons to them particularly the vulnerability to side-channel attacks and their complex requirements making them a hassle to integrate. The solution is to use constant-time operations locally, making it impossible to extract information through such attacks. Consequently, the Arcium Network's MPC implementations are designed to operate in constant time.
Multi-Party Execution Environments or MXEs
It is an environment which dictates a set of configurations where computational tasks or MPC tasks can be carried out. These MXEs are created by the users or computation customers to help define their operations for the task being computed. The MXEs include everything from inputs, outputs, which cluster the MXE should use etc.

The great part of these MXEs is that you can make either single-use MXEs or persistent ones. A single-use MXE can only be used for one computation (duh?) after which it is automatically discarded. Persistent MXEs on the other hand can be used multiple times in the future.
Role of Solana
Let's revisit what Arcium is - a parallelized confidential computing network. Parallelized simply means that Arcium operates as a seperate network running parallely to Solana. Transactions via Arcium are secured via Zero-knowledge proofs or zk-proofs which are then sent to Solana for verification. These zk-proofs confirm the validity of the transactions without decrypting the data, ensuring that the information remains secure, which is the intended purpose of the system.

Remember how Arx nodes had computed the output via MPC tasks. That output is your Zero Knowledge proof or zkp or zk-proof. As straightforward of a nomenclature as it can be, the term "Zero-Knowledge Proof" implies that the party or sender, sending the output (in this case, an Arx node) can prove to the receiver or verifier (a Solana validator) that the transaction is legitimate without revealing the actual content of the transaction.
In this case, Solana is your consensus layer i.e the layer that validates the transaction.
Rewards
As mentioned above these Arx nodes or operators must earn reward for doing all this right? Correct and that's where Solana comes in. Solana validates all these transactions and thus either reward the nodes for the work they've done or penalise them for misconduct or misbehaviour which is known as Slashing.

As we said above, Arx operators provide hardware and a proportional amount of staked tokens to compute the transactions and thus earn reward for doing so. The reward that they get is then given to them based on the job that they've done which is dependent on the computational resources that they provide.
You see how all of this is interconnected?
Third Party Delegators
If you've been involved in Solana, you'll know that users can stake their $SOL with validators and earn a portion of the fees that they earn right? This is called staking. Well, you have third party delegators doing a similar thing here. These delegators delegate or stake their tokens with an Arx Node thus getting a share of the rewards that the Arx node gets. However, to do so, Arx operators charge these delegators a fee as they're the ones providing the physical infrastructure.
In addition to the fees charged, these third party delegators are also liable to be slashed in case of any misconduct.
Now that we have all the pieces defined, let's understand how things work on the backend as well as how easy it looks for the user.
Working Cycle overview
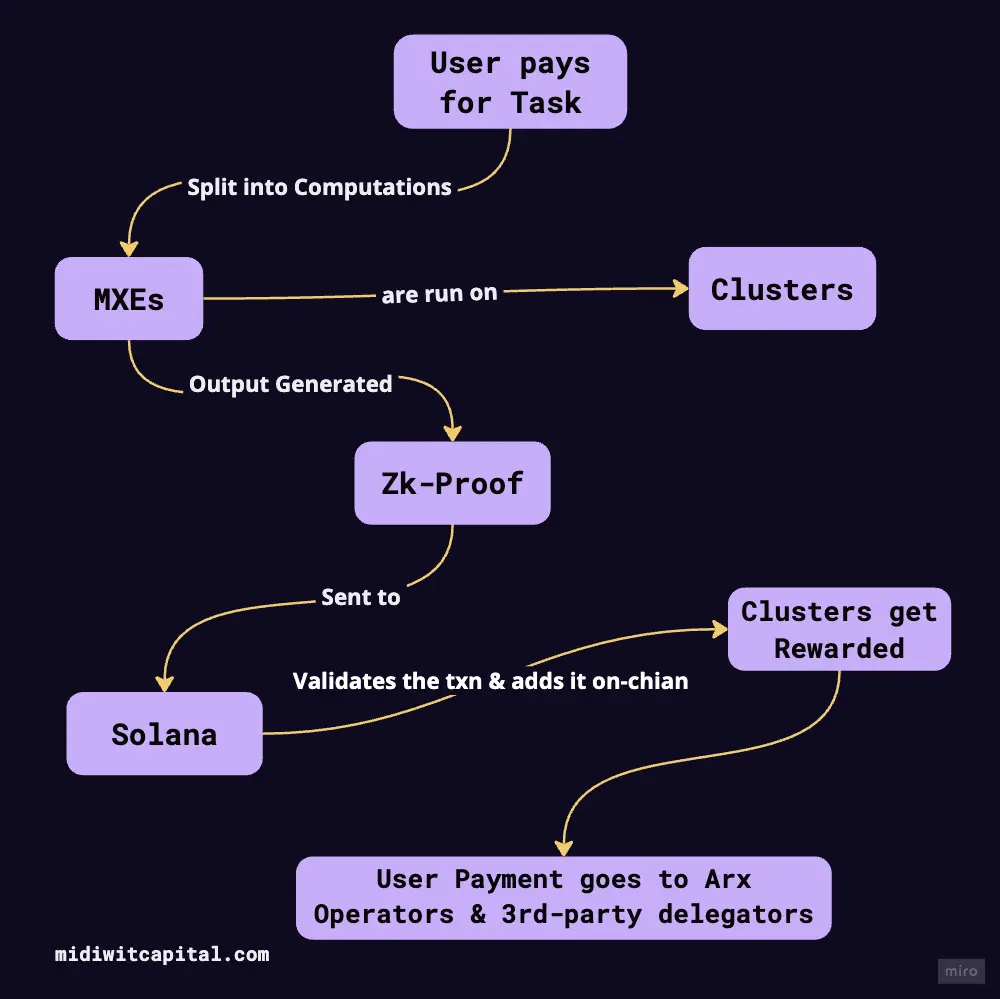
Tasks are split into computations and executed in MXEs based on the parameters set. These MXEs are run on clusters which as mentioned above are groups of Arx nodes. Once the computation is done, a zk-proof of the computation is sent to Solana to validate the transaction.
After Solana validators validate the transaction, it gets added to the blockchain, and the Arx nodes get rewarded for their work. The user's payment is then directed to the Arx Operators and third-party delegators.
Use Cases
We all know how important privacy is and thus while Arcium can help in almost every sector, let's understand a few primary ones given the current on-chain scenario.
AI and Data processing
The current surge in data demand especially for training AI models has raised significant concerns about data storage and its privacy i.e who all can access the data being used to train these models? Given these concerns, it's only natural that Arcium is seen as a pivotal player in this space.

Arcium addresses these concerns by allowing organizations to train their AI models on sensitive data that would be out of reach of centralized entities and thus won't have any need to compromise privacy.
Edge Computing
The current lack of infrastructure to process the vast amounts of data needed for AI training has led to the rise of edge computing AI. Devices at the edge of the network collect and process massive amounts of sensitive information, making confidential networks like Arcium essential for ensuring data privacy and security.
Federated Learning
Arcium also supports the growing system of federated learning, where multiple organizations combine their data to train AI models in a decentralized manner. This method allows for collaborative training without sharing raw data, preserving privacy.
Arcium’s confidential processing network is a crucial component in making federated learning both secure and efficient.
DeFi space
We've seen the crucial role that Elusiv had played in maintaining privacy for Solana DeFi in 2023 and that's what Arcium can do in the DeFi space - providing a place for private transactions.
Private transactions are beneficial for entities that want their details to remain confidential as well as help in reducing the risk of any sensitive information being leaked thus reducing the chances of any hacks, frauds or malicious activities.
OTC Trading
Applications built on top of Arcium can also enhance the Over-The-Counter or OTC trading experience by providing a confidential network that keeps transaction details secure from third parties.
Decentralized Physical Infrastructure Networks or DePIN
Another blooming sector in the crypto space is the DePIN sector where blockchain meets physical infrastructure and assets like real estate, supply chains, IoT devices etc. to on-chain. Bringing such complex systems on-chain requires robust data privacy, something where Arcium excels and need it at lightning-fast speeds and low transaction costs, something where Solana excels.
For example, the massive amount of data for supply chains, healthcare and medical data can be processed on-chain confidentially making it an ideal network to build on.
It can also be utilised to improve curring voting standards. During the last presidency voting in USA, we heard a lot of rumors about tampering of ballots which is why using Arcium, voting data could be made tamper-proof, ensuring no unauthorized access or leak of any sensitive information.
Real World Assets or RWAs
This can expand into RWAs or Real Word Assets which is an emerging sector in crypto by upgrading the current RWA standards complying with data privacy standards for mainstream adoption given that it is a major concern surrounding this space.
Conclusion
That concludes our deep dive on Arcium (formerly known as Elusiv). Addressing privacy and confidential computing concerns, in our opinion, Arcium is a pretty big deal as it not only has the potential to take DeFi to a step further but also help grow the DePIN pie. In this blog, we delved heavily into their tech stack and how Arcium utilizes MPCs, TEEs, zk-proofs and Solana as a consensus layer to make this privacy network a reality.
Arcium is currently outreaching to applicants for testing their Private Testnet beta and you can sign up by joining Arcium's Discord and if you're interested in what they're doing you should definitely sign up for it.
We are beginning the outreach process to Private Testnet applicants! ☂️🤝
— Arcium ☂️ (@ArciumHQ) June 26, 2024
If you applied, keep an eye on your inboxes as we will communicate the next steps.
Questions? Join our Discord here: https://t.co/c21kGokpN3
With that, we conclude the blog and we hope that you enjoyed our deep dive on Arcium. If you're a developer looking to get started on Arcium Network, you should definitely visit their documentation!
Until next time anon. Don't midcurve things!
Midwit out!
If you enjoyed reading this blog, please do share it so that we can get some dopamine and Arcium gets eyes on what they're building! 🫡
References
- Website: https://arcium.com/
- Arcium's Documentation: https://docs.arcium.com/
- Blog: https://blog.arcium.com/
- X (or Twitter): https://twitter.com/ArciumHQ